JWT Claim Headers
Summary
The JWT Claims Headers setting allows you to pass specific user session data to upstream applications as HTTP request headers. Claims forwarded with JWT Claims Headers are not signed by the Authorization Service (unlike the X-Pomerium-Jwt-Assertion header).
Forwarding a claim with JWT Claims Headers adds the claim to the X-Pomerium-Jwt-Assertion header if the claim is not already included in the assertion header. Both JWT Claims Headers and the signed assertion header are forwarded with the pass_identity_headers setting.
How to configure
- Core
- Enterprise
- Kubernetes
| Config file keys | Environment variables | Type | Usage |
|---|---|---|---|
jwt_claims_headers | JWT_CLAIMS_HEADERS | string | optional |
Examples
jwt_claims_headers:
X-Email: email
X-Username: user
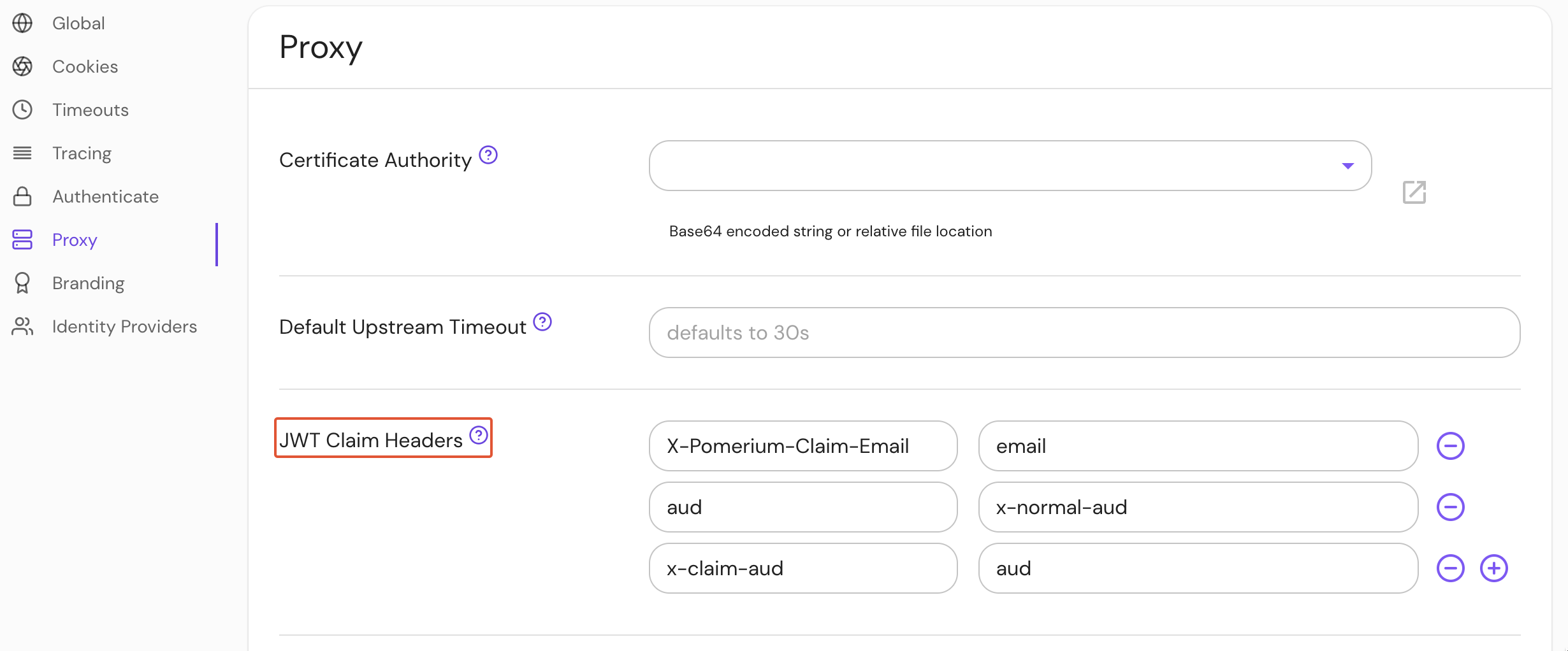
Format JWT Claims Headers in the Console:
| Parameter name | Type | Usage |
|---|---|---|
jwtClaimHeaders | map of strings | optional |
Examples
jwtClaimHeaders:
X-Email: email
X-Username: user
Format JWT Claims Headers
Any claim in Pomerium’s session JWT can be placed into a corresponding header and the JWT payload for upstream consumption. Claim information is sourced from your identity provider and Pomerium’s own session metadata.
The header will have the following format:
X-Pomerium-Claim-{Name}, where {Name} is the name of the requested claim. Underscores will replace dashes. For example, X-Pomerium-Claim-Given-Name.
Customize header names
The JWT Claims Headers setting allows you to customize claim headers with a nested object:
jwt_claims_headers:
X-Email: email
X-Username: user
The JSON payload from this example would look similar to the sample data below:
"X-Email": [
"user@example.com"
],
"X-Username": [
"user"
]
Use this option if you previously relied on x-pomerium-authenticated-user-{email|user-id|groups}.
To pass static values as request headers to the upstream service, see Set Request Headers.